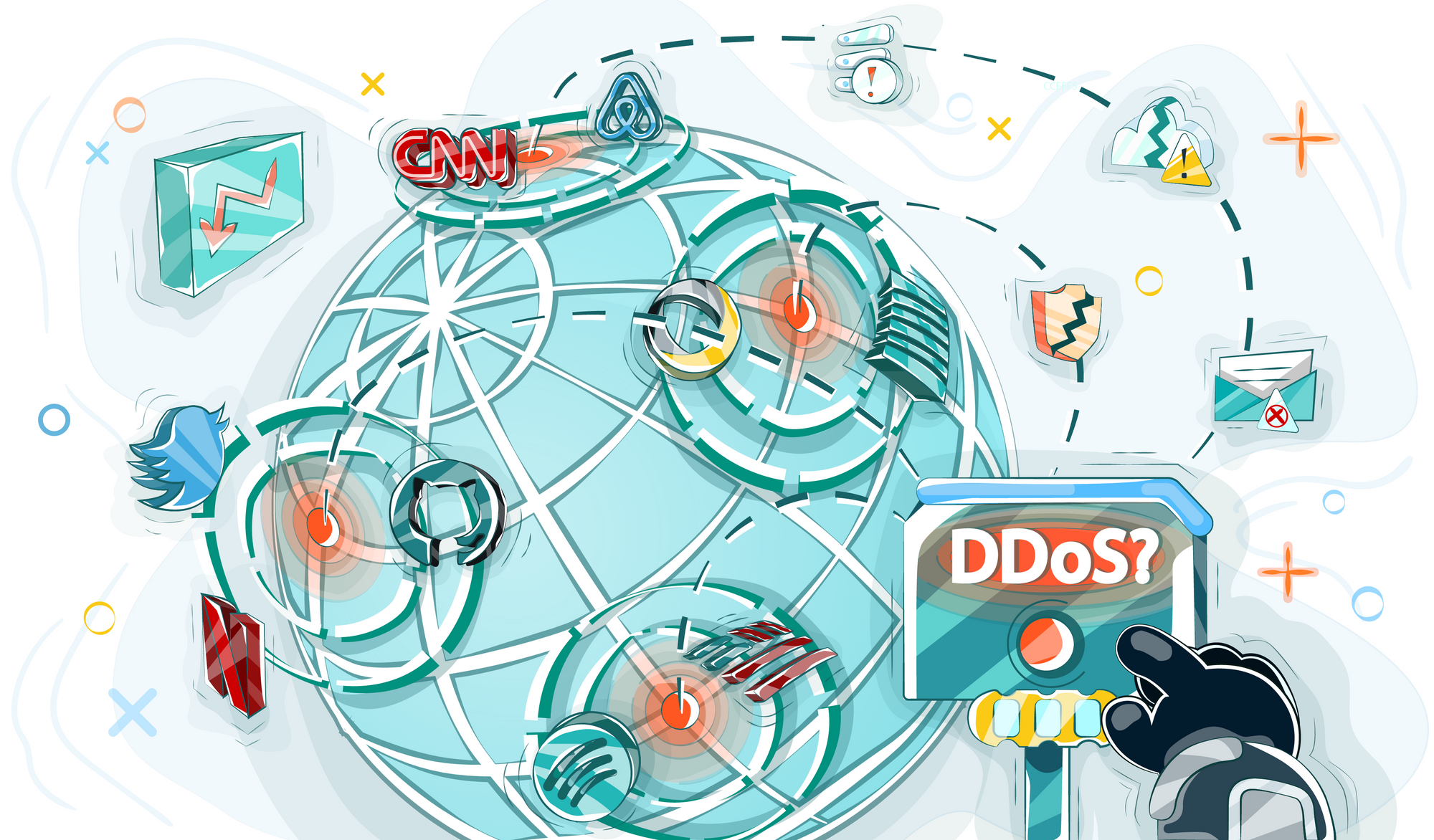
If you have your own website or application, then you surely understand what a DDoS attack is and what consequences it can lead to. In case you have not understood it fully yet, we have prepared some materials for you that will help you to understand why such attacks are organized and why it is worth automating protection.
Let's assume that the cyberattack did hit you. This can happen to anyone - even to large corporations that use enhanced measures to protect their platforms. So, how to determine that somebody is trying to "lay down" your website? And what do you need to do if you are the victim of a DDoS attack already? Let's take a closer look at this problem.
How to understand that a DDoS attack is targeting your site?
There are several types and levels of DDoS attacks. If we generalize them all, the definition of a DDoS attack is the following: the cyberattack aimed at the deliberate overload of the site. The site does not cope with too high traffic. As a result, this platform becomes inaccessible to visitors or periodically issues errors when trying to access it. It is also worth mentioning that DDoS attacks lead to a denial of service - this is how the abbreviation DDoS (Distributed Denial-of-Service Attack) stands for.
For example, the capacity of your resource per day is 10 thousand. Usually, it is visited by half of the indicated number, so there are approximately 5 thousand visits. At the moment of a DDoS attack, you receive 50 thousand requests per second. In fact, these are not real people, but infected devices somewhere, for example, in Singapore. The resource will allow 10 thousand requests, but everyone else simply will not have access to your site. This is what traffic overload implies.
You can understand that something has gone wrong by the fact that it is impossible or difficult to access your site from any device. But there can be many reasons for lack of access. To independently determine the DDoS attack, you or your employees must know what traffic is on your resource at regular times. Critical changes and many requests from suspicious sources most likely indicate a targeted cyber attack.
If the reason for the lack of access to the resource was a DDoS attack, you will be notified by the hosting provider. You can contact the hoster yourself, and then they will answer you that the site is down due to overloaded traffic.
How to act if your website is experiencing a DDoS attack?
So, the protection of your resource was not enough, and the moment X has already come. Let's have a look at what you can do in this case.
The algorithm one should stick to is the following:
- Self-actions of resource owners.
- Accessing the host.
- Contacting cybersecurity specialists.
Let's take a closer look at each step.
Self-actions of resource owners
Initially, you need to try to do something by yourself. If your resource has become a target of hackers, then you are likely to occupy a high position in the market; therefore, you have a team of specialists. They need to be involved in work. In the first stage, they will minimize the attack on their own. You should set speed limits, and you need to do this in the first minutes after you have noticed a traffic overload. You can also clear the logs, so you will free up more space. If you work with an audience in a specific location, for example, you offer services only in Kazakhstan, restrict IP access from other countries.
Accessing the host
Having tried to minimize the impact of the attack, you need to seek outside help, so the best choice is to contact the hosting provider. If an attack is directed at the resource, the hoster will either notify you himself, or you will need to send a message by yourself. The hosting provider will help you fight off the increased number of requests in order to minimize the risks to other customers of their services. Also, hosts can try to filter traffic.
Contacting cybersecurity specialists
The next stage is to contact specialists who are engaged in cybersecurity and know what measures must be taken if there is a cyberattack. There is an important caveat: a DDoS attack will not last forever.
Ordering hackers for a week costs only about $150, which does not seem too much money. But for large portals, prices are even higher, and the risks of becoming a target for a cyber attack remain as high. If the resource is visited by a million people a day, the price can be 2 thousand dollars a day. Even if the attack is directed at you by large competitors who can afford it, such expenses definitely hit the pocket.
Most likely, a DDoS attack will last from a few days to a week, so the first solution is to wait it out. Most often, owners of rather small portals consider this option. But this is not entirely correct, as 2 or 3 days of downtime of your site will lead to a loss of income and reputation of your business. To avoid threats to hosting neighbors, the provider can block your IP. You will have to spend a lot of time and money on recovery. And if you work with customer data, you may face its loss. This threatens even more costs and can lead to deplorable consequences, up to the closure of the business.
Therefore, if you are the victim of a large DDoS attack, you need to contact specialists to help eliminate it. It will cost you a penny, but the costs will be many times less than in the case of independent elimination of the consequences. To cope with the problem, cybersecurity specialists will redirect requests to their servers that can withstand it. Then, they will be able to filter them.
Being aware of what to do in the case of a DDoS attack, you will be able to prevent harmful consequences. You should be fully aware of it, because no one is immune from cyber attacks, be it GitHub or Amazon. But you can minimize risks even before competitors or malicious hackers try to harm you. For example, one of the largest attacks on GitHub in 2018 brought the service offline for only 10 minutes, and there were no consequences like the loss of user data. It's all about defense. Large companies usually consider it, but security is also needed for a start-up business.
How to minimize the risks of DDoS attacks?
Forewarned is forearmed. Nowadays, DDoS attacks have become commonplace, and thousands of resources suffer from them a day. It's better not to hope that your site will be an exception - unless you use only a business card website and accept orders by phone.
Nowadays, by protecting an online resource, you protect your business. And for the level of security to be really high, it is necessary to do the following:
- Hire a specialist. This should be a person who, at the first signs of a DDoS attack, will know what to do and what actions to take. If an employee responsible for tasks of this kind can only connect monitors at the request of puzzled colleagues from other departments, then solving the problem will take a long time, and the losses will be significant. To minimize risks, it is worth keeping a professional in the staff who understands how to identify such problems, how to deal with DDoS attacks, and what the basic algorithm of action should be. Besides, it is better to hire several specialists who will be able to do something if the cyber attack is launched not by a student who just wants to entertain himself, but by professional hackers.
- Go through certification. Technical security will give you confidence that your data will not be lost. We have already discussed to what extent data loss can affect your business. To avoid this, you need to make sure that your resource meets all the required standards and norms.
- Audit regularly. To get rid of vulnerabilities, you need to know about them. To do this, it's necessary to audit your resource with a certain frequency and analyze how well it is protected.
- Install anti-DDoS protection. We offer protection against DDoS attacks for both virtual and dedicated servers, which involves filtering requests based on geographical distribution with a capacity of 1 TB/s and hardware. Our multi-level cleaning system will help you withstand up to 100 Gb/s, and your resources will be available 24 hours a day.
Statistics on DDoS attacks are constantly growing. According to marketing research, each year number of attacks increases by 200%. To protect your resource, customer data, and business as a whole, you need to know only 2 things: how to minimize the risks of interference and what to do if an attack is already taking place. If you want to order effective protection, contact King Servers and we will help you to prevent the actions of intruders!