Typology of attacks: from classic floods to intelligent multi-vectors
By 2025, cybersecurity isn’t just a technical checklist—it’s a full-on arms race. DDoS attacks, once an occasional nuisance, have morphed into a daily reality for businesses of all sizes. We’ve watched this shift unfold firsthand while working with clients at King Servers, and it’s clear that the game has changed. Attackers are leveraging cloud tech, AI, and botnets to hit harder and smarter than ever before.
In this article, we’ll walk you through how DDoS attacks have evolved, the threats dominating the landscape today, and what it takes to shield cloud-based systems effectively. Along the way, we’ll share insights into how King Servers tackles these challenges, including our DDoS protection for VPS/VDS, which you can explore here: https://kingservers.com/en/ddos-vps-vds/.
By the Numbers: A Shocking Landscape
Link11 dropped a bombshell: 137% increase in DDoS attacks compared to the previous year. And Radware? They're reporting a mind-blowing 550% surge in web-based attacks. Average attack volume? Up by 120%.
These numbers aren’t just statistical noise—they represent real systems under fire, real businesses suffering outages, and real security teams scrambling to respond. We’ve seen it firsthand: even well-prepared companies are feeling the heat. And as attack automation becomes more accessible, these figures are only the beginning. The question isn’t "if" anymore. It’s "how ready are you when—not if—the next wave hits?"

Multi-Vector Attacks: The New Nightmare
These aren't your standard, one-dimensional attacks. We're seeing complex, multi-layered assaults that shift and morph in real time—often combining volumetric, protocol, and application-level tactics within a single campaign. Traditional defenses? They're buckling under the pressure.
In one recent case, we observed a coordinated attack that began with a 300 Gbps UDP flood (L3), immediately followed by a wave of HTTP/2 Rapid Reset requests peaking at over 8 million RPS. All of this was layered with fake DNS lookups targeting recursive resolvers to exhaust upstream capacity. That’s three separate vectors—hitting bandwidth, application logic, and DNS infrastructure—all within 90 seconds.
Here’s what makes these multi-vector attacks so dangerous:
- • Speed: Attack patterns change on the fly. Some switch vectors every 15–30 seconds.
- • Scale: Combined traffic often exceeds 500–700 Gbps with ease.
- • Stealth: Application-layer attacks now mimic real user behavior, slipping through basic filtering.
- • Saturation: Even cloud-native setups with autoscaling struggle to keep up under sustained load.
We used to talk about DDoS in terms of "when," but multi-vector attacks force a new mindset: "how many layers can we absorb before impact?" At King Servers, we now design protection schemes assuming at least two simultaneous vectors. Anything less is a gamble.

Application Layer Attacks (L7)
Fintech got hit hard—and it wasn’t a coincidence. Almost half of all L7 attacks in 2024 and early 2025 specifically targeted the financial technology sector. Why? Because that’s where the money, data, and user trust live. These aren’t brute-force floods from a forgotten era. These are precision strikes: low-and-slow request floods, recursive API hits, and bot-driven session initiations that look legitimate until your backend quietly crashes under the load.
And the targeting is disturbingly surgical. Attackers know the endpoints. They know what hurts most. Login pages, payment gateways, user dashboards—we’ve seen all of them fall under sustained L7 pressure. In one real-world case, a fintech client saw a 3.7 million RPS spike over 20 minutes, with 92% of that traffic originating from a distributed botnet using residential proxies and mobile 4G IPs.
To make matters worse, attackers now rely heavily on HTTP/2 multiplexing, leveraging protocol quirks to overwhelm systems with minimal bandwidth usage. Combine that with real-user behavior emulation—think delays, cookie handling, session rotation—and you’re no longer looking at traffic anomalies. You’re looking at digital camouflage.
Modern L7 protection requires a shift in mindset. It's no longer about counting requests per second—it's about contextual analysis, behavioral baselines, and instant mitigation at the edge. Effective systems now track known botnet behaviors, fingerprint suspicious headers, and preemptively challenge dubious sessions before they reach your application logic. Without this level of intelligence, it's almost impossible to differentiate between a malicious actor and a legitimate user during high-velocity, low-signature attacks.
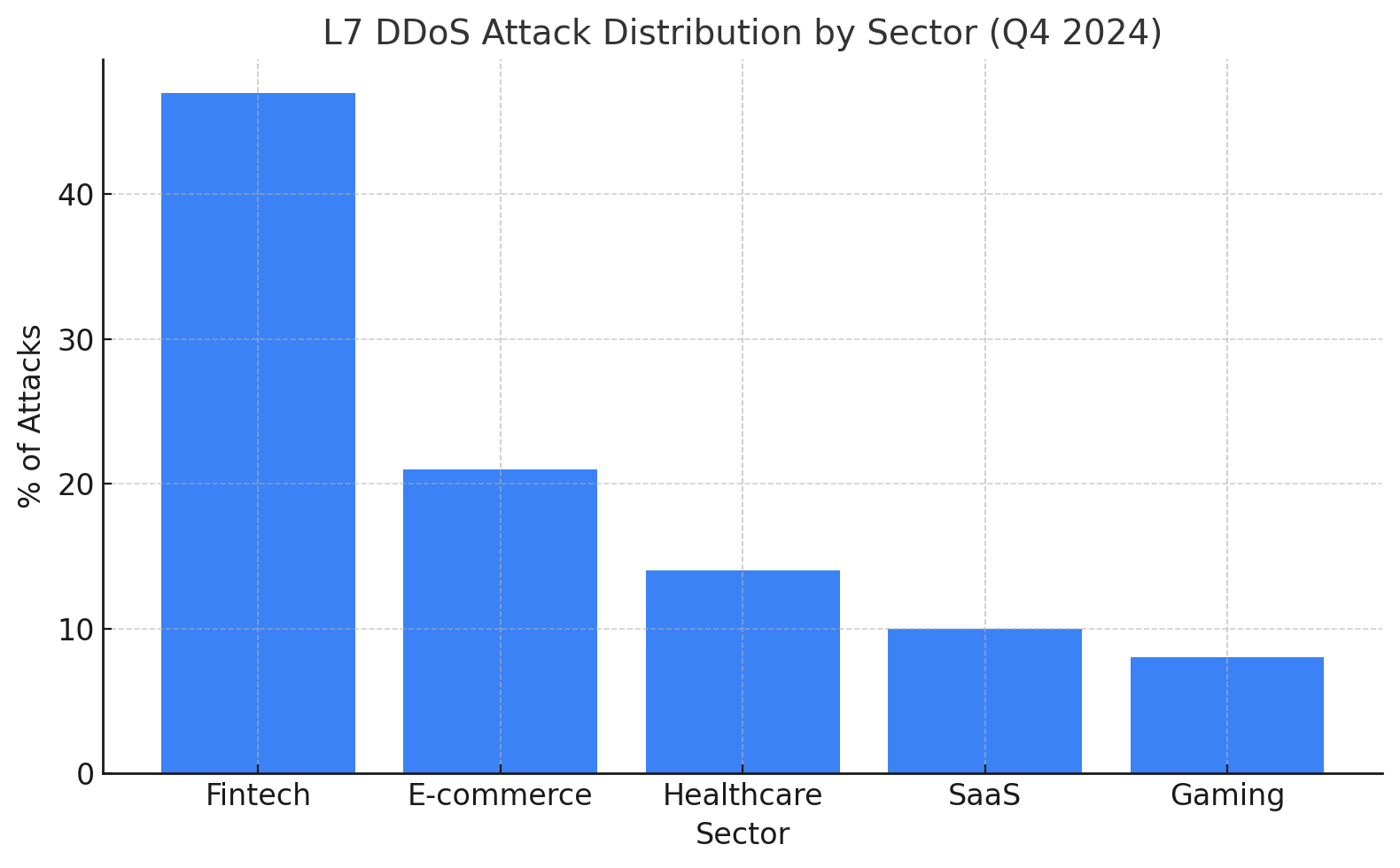
How big is this threat, really?
Take a look at the breakdown below. It shows the sectoral distribution of L7 DDoS attacks recorded in Q4 2024:
As the graph shows, fintech isn’t just in the lead—it’s in a league of its own. And for attackers, that makes it the biggest digital bullseye on the map.
Attack Layers: The Battlefield Breakdown
Network Level Attacks (L3/L4)
Numbers don't lie, and these are brutal. In Q3 2024, we saw an 80% spike in network-level attacks. By 2025, peak speeds hit 446.57 Gbps. It’s like trying to drink from a fire hose—except the water is pure digital destruction.

The Botnet Evolution: A Terrifying Upgrade
Remember when botnets were just a bunch of compromised computers? Those days are long gone. IoT devices and virtual machines have turned botnets into superweapons. We’re talking capabilities 5,000 times more powerful than traditional setups.
Today's botnets are globally distributed, often leveraging residential IPs, 4G mobile networks, and even compromised cloud instances. They’re harder to detect, faster to mobilize, and nearly impossible to take down through traditional blacklisting.
More than 60% of all large-scale DDoS events in late 2024 were powered by botnets comprising over 100,000 devices. In one attack we observed, a botnet coordinated over 8.5 million requests per second using smart TVs, IP cameras, and edge routers.
What’s worse, many of these modern botnets are modular. They can switch between UDP flooding, HTTP request bursts, and DNS amplification on the fly—based on how your infrastructure responds. They measure your defenses in real time and pivot tactics accordingly.
In short: we’re not dealing with zombies anymore. We’re dealing with intelligent, shape-shifting swarms that test and exploit your weakest link—faster than most defenses can adapt.
DDoS Attacks in 2025: What’s New?
A few years ago, DDoS attacks were mostly about overwhelming servers at the L3/L4 levels. Now? They're smarter, faster, and more devastating.
- • L3/L4 Attacks (Network and Transport Layers): Old-school but dangerous. Now powered by cloud VMs instead of IoT alone. Average volumes? 500+ Gbps.
- • L7 Attacks (Application Layer): Focused on exhausting app resources. We've seen attacks hitting 10 million RPS.
- • Botnets: Machine learning now helps them mimic humans and bypass CAPTCHA.
- • DNS Flood: From query floods to DNS amplification—cloud-dependent services suffer most.
- • Multi-Layer Attacks: L3 attacks distract; L7 delivers the real blow. Single-layer defenses? Outdated.
As the cloud boom continues, the attack surface grows—but so do the defense strategies.
Where Are Attacks Coming From?
DDoS threats don’t just emerge from the shadows—they have geographic fingerprints. While the tools may be global, the traffic often concentrates in regions with high-density botnets, exposed IoT ecosystems, or accessible cloud infrastructure. The map below highlights the primary countries from which large-scale DDoS activity originated in 2025.
It’s a reminder that this isn’t a local issue. It’s a distributed war, and understanding where attacks come from is the first step in knowing how to defend against them.
Protecting the Cloud: What Makes It Different?
Cloud environments are powerful but complex. At King Servers, we manage cloud VPS/VDS infrastructure daily and have identified key challenges:
- • Distributed Nature: More nodes = more points to secure.
- • Dynamic Scaling: Can backfire during an attack, increasing costs without solving the problem.
- • Provider Reliance: Filtering often depends on your host. That’s why built-in DDoS protection matters.
Start with a map of your weak spots. What’s business-critical? That’s your priority.

Modern Anti-DDoS Strategies
By 2025, the anti-DDoS arsenal is stronger than ever. Here’s what works:
- • Layered Filtering: Network-level scrubbing + WAF for apps = full-spectrum defense.
- • Cloud CDN and Proxies: Spread traffic, hide IPs. Our King Servers solution does just that.
- • Behavioral Analysis: AI detects and blocks non-human traffic. Built into our system.
- • Geo-Blocking and Rate Limits: Simple, effective add-ons.
- • Redundancy: Spin up backup servers instantly in the cloud.
Our DDoS protection for VPS/VDS handles attacks up to 1 Tbps and gives clients visibility and control—not a black-box solution.

Practical Steps to Secure Your VPS
Here’s how to prep for modern DDoS:
sudo apt update && sudo apt upgrade -y
sudo ufw allow 80/tcp
sudo ufw allow 443/tcp
sudo ufw deny in from 0.0.0.0/0 to any
sudo ufw enable
ab
or
Siege
to find your system’s limits.
These steps won’t make you invincible, but they raise the bar. And that’s often enough.
Looking Ahead
DDoS in 2025 isn’t just a risk—it’s a certainty. But you don’t have to face it unarmed. At King Servers, we help clients build resilience into every layer of their infrastructure. Our tools evolve with the threat landscape, and our team is always ready to support you.
Cybersecurity is never finished. Stay alert, test often, and partner wisely. Need help? Our support is available 24/7 via chat or ticket.
Let’s make your cloud setup not just fast and scalable—but bulletproof.